What is Blockchain Technology?
We can consider the blockchain technology as the 5th disruptive computing paradigm on the Internet history.
In the blockchain technology we can bridge the gap between the demand and supply of any work effectively. Because when the demand is created people can approach the market directly without the intermediary. The opportunities are wide open with different opportunities and possibilities.
The work which need to be done without third party intervention can be done with blockchain technology efficiently. The documents which needs high security can be maintained with blockchain technology.
One should learn how to implement and when to implement a blockchain
Blockchain Technology includes Cryptographic techniques, Peer-to-Peer Network mechanisms to create and deploy the blockchain
Just like the index in the book, the hash includes the information about data in the particular block, the blocks are secured using various hashing algorithms. Secure Hashing Algorithm(SHA), Cryptographic algorithms . That will create key pair as Public key and Private key. Those keys will decide the permission to use the data.
Data will be encrypted using cryptographic algorithms and the details will be stored in the hash.
Blocks
The data which entered and mined once will create the block.
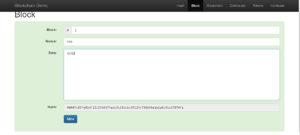
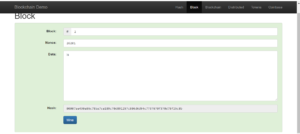
To see this hash value clearly on your own, please refer AndersBrownWorth’s web page.
In the above example, the sentence “God is Great” is segregated into blocks. In block1- the data “GOD” is stored, in block2 – the data”is” is stored, in block3 – the data “great.” is stored. Note that for a computer the special characters like space, “.” are also data, if we change that the hash value will change and in pattern matching also it will show error only, it will match if the data is exactly matching each other. It will not only consider the verbal data but also the other special characters.
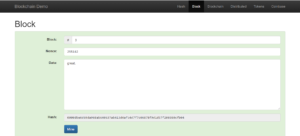
Blockchain
The blocks will create the blockchain which will connect through the hash value.
You may notice the hash value for each block, it is different. When it forms the chain block1’s hash value will be denoted in the block2, the block3 will carry the hash value of the block2 and so on . Thus the chain will continue with the hash values.
Hash
SHA- 256(Secure Hash Algorithm) is the widely used hash function for blockchain technology.
The process of hashing validate the network transactions.
It secures your data, it create a random set of characters as key, that others cannot guess easily.
Let us see the other terms used in the blockchain technology.
Nonce
A new block must contain the proof of work(PoW), that has to be accepted by the other people in the peer to peer network. The PoW needs this Nonce (Number used Once) will be found out by the peers to acknowledge the new block.
Nodes
Each system or computer which is participating in this Peer-to-Peer network is called nodes.
Token
Very often people have used “tokens” in the public places. Most of the people might have the experience of using tokens in their daily life. Example clock rooms, safety lockers. When you use the token, you might have stored the details with the confidential person or system, while doing the work you will do it with your token identification not with the original data.
In this blockchain technology the token will be created for each block.
Token is an object which represents the particular data, the object can be shared and the data need not to be shown to the third party or in the public media platform. Token represents the set of rules for encrypting the data. Thus the data can be transmitted secretly with the cryptographic security techniques. They can be categorized as creator token and community token.
A non-fungible token (NFT) is a unique and non-interchangeable unit of data stored on a blockchain, a form of digital ledger. Non-fungible tokens (NFTs), has been used in video games for monetization. NFTs use a digital ledger to provide a public certificate of authenticity or proof of ownership, but do not restrict the sharing or copying of the underlying digital files.
Mining
Mining is a record-keeping service done through the use of computer processing power. Miners keep the blockchain consistent, complete, and unalterable by repeatedly grouping newly broadcast transactions into a block, which is then broadcast to the network and verified by recipient nodes.
Hyperledger
Hyperledger is a global enterprise blockchain project that offers the necessary framework, standards, guidelines, and tools to build open-source blockchains and related applications for use across various industries.
It’s main aim is creating industry-wide collaboration for developing high-performance and reliable blockchain and distributed ledger-based technology framework that could be used across the various industry sectors to enhance the efficiency, performance, and transactions of the various business processes.
The fields of finance, gaming, Internet of Things, Artificial Intelligence are highly using Block chain technology effectively and creating data records.
This distributed ledger continuously registering huge amount of immutable data.
Smart contract
A smart contract is a computer program or a transaction protocol which is intended to automatically execute, control or document legally relevant events and actions according to the terms of a contract or an agreement.
smart contract are typically written in a Turing-complete programming language. Example: Ethereum smart contract written in the programming language Solidity.
It will help us to avoid the third party interventions and enhancing the security features. A smart contract must be validated and audited properly to maintain the security and secrecy of the data. Security features must be uncompromised to possess your data and to get your profit
Wallet
A wallet will store the digital information which is needed for transaction. A wallet consists of public key, private key, tokens, address etc. you need to use the wallet address during a transaction, in that the tokens will be uploaded. The public key will be shared during your transaction, but the private key should not be shared like the pin number of your bank account, it is for your personal use only. But one important thing you need to remember that, if you miss the private key you cannot recreate it again. As it is decentralised network and transactional data is immutable, keys cannot be changed or recreated.
Network
Peer to peer network is used to implement the blockchain technology, which will help to maintain the data consistency and relevancy. The network work as a decentralised and distributed network.
The above are the important terms in the blockchain technology. The basic functionality includes all these terms of work to create the blockchain, to deploy and to share and trade the blockchain. You may come across these terms with the word “crypto”, that is the application created using this technology. Example : Cryptocurrency, Cryptowallets, Cryptocoins.
Types of Blockchain
As blockchain is decentralised, it is essential to create some level of authentication to secure the businesses. They preferred to create separate a separate blockchain to work with. The types of blockchains are categorized under Permissioned and permissionless
Public blockchains
A public blockchain has absolutely no access restrictions. Anyone with an Internet connection can send transactions to it as well as become a validator . Example: Bitcoin blockchain and the Ethereum blockchain
Public Blockchain allows anyone to join and participate in its activities. But the security is questionable and it is vulnerable for hacking, stealing tokens and etc.
Private blockchains
A private blockchain is permissioned. One cannot join it unless invited by the network administrators. Participant and validator access is restricted. Distributed Ledger (DLT) is normally used for private blockchains. Some examples of private blockchains are the business-to-business virtual currency exchange network Ripple and Hyperledger, an umbrella project of open-source blockchain applications.
Consortium Blockchains
Consortium blockchains are permissioned blockchains governed by a group of organizations, rather than one entity, therefore, enjoy more decentralization than private blockchains, resulting in higher levels of security.
Hybrid blockchains
Hybrid blockchains are partially permissioned and partially permissionless blockchains that are controlled by a single organization, but with a level of oversight performed by the public blockchain, which is required to perform certain transaction validations. Example : IBM Food Trust.
Software requirements
Platforms
Different platforms are available for different application of blockchain, some of them are company based, some of them are software based.
Programming Language
As the basic concept of blockchain is object oriented and distributed, the language which is object oriented and distributed is mainly used to create and deploy blockchain. Bitcoin is created using C++. Ethereum is using the language Solidity. Blockchain Programming Languages are used with cryptographic techniques. The versions of Java such as NodeJs, ReactJs, IdentificationJs are also highly used to create blockchain and smart contract. Javascript, Python, Ruby are also used for creating blockchain. Some of the other examples are Truffle, ganache etc.
Hardware requirements
The considerable facts for hardware requirements are RAM storage, Storage capacity, Bandwidth, Power consumption, Cooling system, efficiency, maintenance cost etc. if a person can afford the needed quality of hardware set up for deep mining they can do it. Otherwise when there is need that means at the beginning level you may not need it, but after you reached some growth if you need you can hire from the market by paying the rent. At the initial stage any computer with good computing power is good to use.
Benefits of Blockchain Technology
High Security
Secrecy and security is maintained by Cryptographic techniques and algorithms without human intervention, if there is an error in any of the pattern matching, the particular transaction will not be acknowledged by the other peers in the network, so that it is not easy for the fraudulent people to enter into the network. You have control over your own data with the private key.
Immutability
As the transactional data is immutable, data is static and cannot be changed over time. The history of transactional data will be registered automatically using automation techniques. So no need to appoint a person to maintain the data.
Different category of people are using blockchain technology like business man, educationist, researchers, lawyers and etc. Blockchain technology is going to support all category of people. Let us learn those details in the future articles.
Pingback: What is a Blockchain? | Edujem
Pingback: What is Cryptocurrency? | Edujem
Pingback: Which Programming Languages supports Blockchain? | Edujem